Icloud Couldnã¢â‚¬â„¢t Save Reply Try Again

iCloud 101
In fact, the iCloud is not a single service only general marketing name for a number of cloud-based services from Apple. These include the syncing of settings, documents and photos, Discover My Telephone to locate lost or stolen devices, iCloud Backup to backup your information to the cloud, and at present it's also iCloud Keychain for secure syncing of passwords and credit menu numbers betwixt iOS- and OS Ten-based devices.
Each iCloud service is hosted at its own 3rd level domain, such as pXX-keyvalueservice.icloud.com, where Xx is the number of the server grouping responsible for processing the requests of the current user; for various Apple IDs, this number can be dissimilar; typically, the newer is account, the greater is the number in this counter.
iCloud Security Code
Before diving into analysis of iCloud Keychain, we will pay more than attention to the configuration of the service. When enabling iCloud Keychain, the user is asked to retrieve upwards and enter his/her iCloud Security Code (iCSC). By default, the input form allows you to utilise a four-digit numeric code, only past clicking the "Avant-garde Options", yous tin can employ a more complex code or even allow your device to generate a stiff random lawmaking for you.
Now nosotros know that, in iCloud Keychain, the information is protected by iCSC. Let's endeavor to empathise how exactly this protection is implemented.

By default, iOS prompts you to use a four-digit security lawmaking
Traffic Interception or a Man-in-the-Middle
When you analyze the network services, the first footstep frequently includes gaining access to the network traffic between the client and the server. In case of iCloud, we have ii pieces of news for you: bad and good. The bad news is that all traffic (or at least the overwhelming part of information technology) is protected past TLS / SSL, that is, it is encrypted and a conventional passive attack would non let to "read" it. The proficient news is that Apple made a souvenir to all those who want to further study iCloud considering it does not utilize the certificate pinning and, therefore, allows y'all to rather easily organize a man-in-the-middle attack and decrypt the intercepted traffic. All yous need to exercise is this:
- Place the iOS device that you want to use in the experiment into the aforementioned Wi-Fi network as the intercepting computer.
- Install the intercepting proxy server (such as Burp, Charles Proxy or any similar server) on the computer.
- Import the TLS / SSL document of installed proxy server (encounter details in the Aid for specific proxy server) to iOS device.
- In the Wi-Fi network settings on iOS device (Settings â†' Wi-Fi â†' Network Name â†' HTTP Proxy), specify the IP-address of intercepting reckoner in Wi-Fi network and the listening port of the proxy server.
If washed correctly, this volition allow yous to go the full view of traffic between the device and iCloud. The interception of this traffic will conspicuously show that iCloud Keychain is based on two iCloud services: 'com.apple.Dataclass.KeyValue' and 'com.apple tree.Dataclass.KeychainSync' â€" and, when initially and subsequently enabled on other iOS devices, it communicates with these services.
The offset service is not new and was among the start features of iCloud; it is widely used by applications to sync settings. The 2nd service is new and, probably, was adult specifically for iCloud Keychain (although, theoretically, its functionality allows to utilize information technology also for other purposes). Let'due south have a closer look at these services.
com.apple.Dataclass.KeyValue
Every bit I already mentioned above, this is one of services used by iCloud Keychain. Many existing applications utilize it to synchronize some pocket-size amounts of information (settings, bookmarks, etc.). Each record stored by the service is associated with the Package ID and the store proper name. Appropriately, to obtain the stored data, you will also need to provide these identifiers. In iCloud Keychain, this service is used to synchronize Keychain records in the encrypted grade. A detailed clarification of this process is provided in sections on Keychain Syncing and How Keychain Syncing Works in the document "iOS Security".
Keychain Syncing
When the user enables iCloud Keychain for the showtime time, the device creates a circle of trust and syncing identity which includes a public and private key for the current device. The public key of this pair is placed in the circle of trust and the circle is signed twice: first, by the individual cardinal of syncing identity and next by an asymmetric key (based on Elliptic Curve Cryptography) generated from the user password in iCloud. Also, the circle stores the parameters for calculating the key from the countersign, such as salt and the number of iterations.
The signed circumvolve is saved in Primal/Value store. It cannot be read without knowing the user countersign in iCloud and cannot be changed without knowing the individual key of one of the devices added to the circle.
When a user enables iCloud Keychain on some other device, this device communicates with Key/Value store in iCloud and determines that the user already has a circle of trust where the new device is not included. The device generates synchronization keys and a receipt for requesting the membership in the circle. The receipt contains the public key for syncing the device and is signed by a key generated from the iCloud user countersign by using the cardinal generation parameters retrieved from Primal/Value store. Next, the signed receipt is placed in the Cardinal/Value store.
The first device can meet the new receipt and displays a message for the user that prompts him/her to add a new device to his/her circle of trust. The user enters his/her iCloud password, and the receipt signature is checked for validity. This proves that the user who generated a request to add the device has entered the correct password when creating the receipt.
In one case the user confirms the addition of device to the circle, the outset device adds a public fundamental for syncing the new device to the circle and, again, signs information technology twice by using its private synchronization key and the cardinal generated from the iCloud user password. The new circle is stored in iCloud, and the new device similarly signs it.
How Keychain Syncing Works
Now, there are two devices in the circle of trust, and each of them knows the public keys for syncing the other devices. They begin to share Keychain records via Key/Value store in iCloud. If the same record is present in both devices, the priority will exist given to the one with later modification time. If the record modification time in iCloud and on the device is the same, the record is not synced. Each synced record is encrypted specifically for the target device; it cannot be decrypted past other devices or Apple. Furthermore, the record is not permanently stored in iCloud â€" it is overwritten by the new synced records.
This process is repeated for each new device added to the circle of trust. For example, if a third device is added to the circle, the confirmation request will exist displayed on other two devices. The user can confirm the add-on on whatever of them. As you add more devices, each device of the circle is synced with the new 1 to brand sure that the set of records is the same on all devices.
It should exist noted that not the entire Keychain is synced. Some records are tied to a device (e.k., VPN accounts), and should not leave the device. Only the records with the attribute 'kSecAttrSynchronizable' are synced. Apple tree has gear up this aspect for Safari user data (including user names, passwords and credit card numbers) and for Wi-Fi passwords.
In addition, the records of third-party applications are not synced past default. To allow their syncing, the developers must explicitly set the attribute 'kSecAttrSynchronizable' when adding the record to Keychain.
iCloud Keychain operates two stores:
- com.apple.security.cloudkeychainproxy3
- Bundle ID: com.apple.security.cloudkeychainproxy3;
- com.apple.sbd3
- Package ID: com.apple tree.sbd (SBD stands for "Secure Backup Daemon").
The first store is apparently used to maintain a list of trusted devices (devices in the circle of trust that are allowed for password syncing), to add new devices to the list and to sync the records betwixt devices (in accordance with the mechanism described above).
The second shop is designed to backup and restore Keychain records on new devices (for example, when the circle of trust has no other devices) and contains encrypted Keychain records and related information.
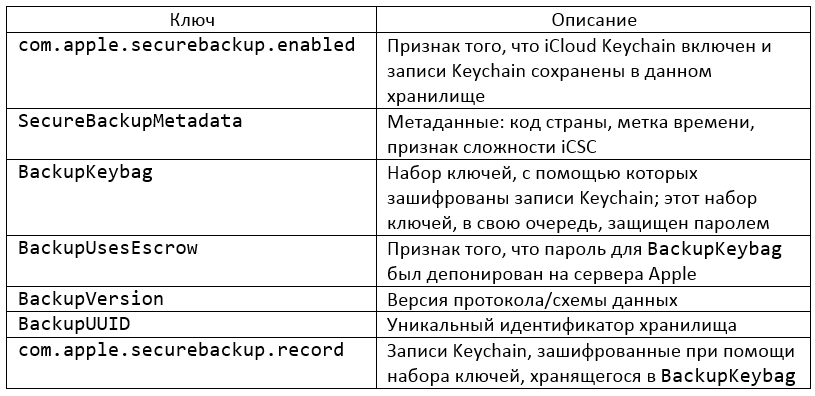
Entries in the store 'com.apple.sbd3'
Therefore, the Keychain records are stored in a regular Key/Value store ('com.apple.securebackup.record'). These records are encrypted past using a set of keys stored in the aforementioned place (BackupKeybag). Simply this set of keys is protected past a password. Where does this password come from? What is the Apple countersign escrow service? Allow's try to figure it out.
apple.Dataclass.KeychainSync
This is a new service, which appeared relatively recently: for the outset time, information technology was supported in beta versions of iOS 7, then it disappeared in iOS 7.0-7.0.2 only to be re-added to iOS 7.0.3, which was released simultaneously with Os X Mavericks. This is the password escrow service that I mentioned earlier (the service is hosted at pXX-escrowproxy.icloud.com).
This service is designed to safely store the user secrets and allows the user to recover these secrets subsequently successful authentication. Such successful authentication requires the following:
- iCloud authentication token obtained in exchange for Apple tree ID and countersign during the initial authentication in the iCloud (this is a standard authentication method for well-nigh iCloud services);
- iCloud Security Code (iCSC);
- Six-digit numeric code communicated by the Apple servers to mobile telephone number associated with the user.
In theory, everything looks good, just to determine whether the theory matches the practice, nosotros volition demand to audit the client of escrow service. In iOS and Os X, this programme is called 'com.apple.lakitu'. The description of its contrary technology and inspect is beyond the scope of this commodity, and so, let's become direct to the results.
Bachelor Commands
The inspect of 'com.apple.lakitu' allows you to identify a list of commands used past the escrow service. On the relevant screenshot, you tin run into the commands and their descriptions. I would specially like to draw your attention to the last command. It allows you to change the phone number associated with the electric current account. This command makes significantly less reliable the multi-cistron authentication that is used when recovering iCloud Keychain (Apple ID password + iCSC + device), every bit information technology allows to exclude one of the factors. Information technology is also interesting to note that the user interface in iOS does not allow you to run this command â€" it simply does not have that option (at least, I couldn't find it).
A characteristic of this command, that distinguishes it from all others, is that information technology requires the authentication with the Apple ID password and will not piece of work in instance of authentication with iCloud token (other commands work with the authentication token). This provides boosted protection for this control and shows that the system designers have taken some steps to improve its security. However, it is not clear why this command is available in the system at all.
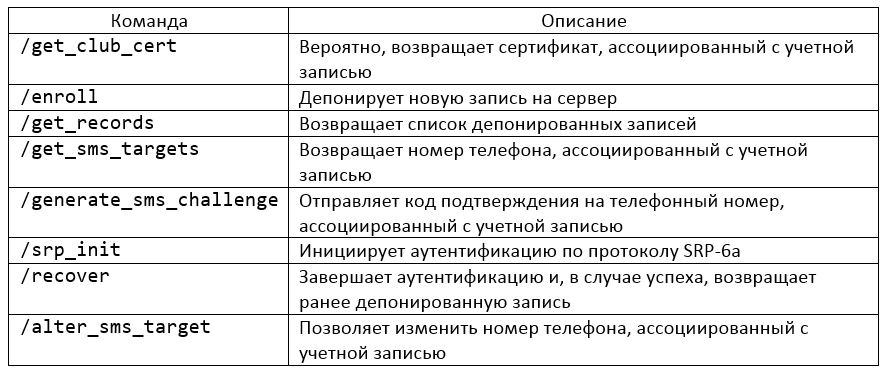
Commands supported by 'com.apple.Dataclass.KeychainSync' service
Restoring Escrowed Data
The post-obit protocol is followed to obtain the escrowed data:
- The client requests the list of escrowed records ('/get_records').
- The customer requests the associated telephone number where the server will send a confirmation code ('/get_sms_targets ').
- The client initiates the generation and delivery of confirmation code ('/generate_sms_challenge').
- Once the user has entered iCSC and the confirmation code received from SMS, the client initiates the authentication attempt by using SRP-6a ('/srp_init').
- After receiving a response from the server, the client makes the calculations prescribed by SRP-6a and requests the escrowed data ('/recover').
- If the client has successfully passed the authentication, the server returns the escrowed data after encrypting it with the key generated in the process of running SRP-6a (if this protocol has run successfully, then both the server and the client have calculated this shared central).
Information technology is important to note that the telephone number obtained in step ii is used exclusively for the needs of the user interface, that is, to evidence the user the number where the confirmation code will be sent and, in step 3, the client does not communicate to the server the number for sending the confirmation code.
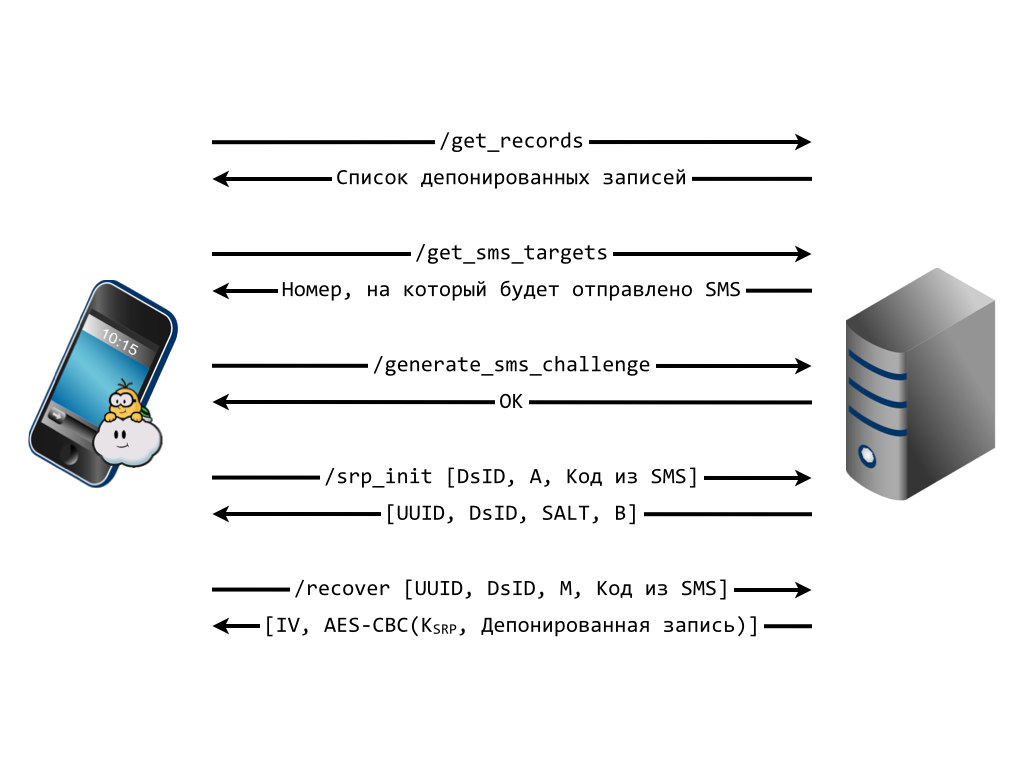
Recovering the escrowed record
Secure Remote Password
In footstep iv, the client initiates SRP-6a protocol. SRP (Secure Remote Password) is a password authentication protocol protected against eavesdropping and man-in-the-middle attacks. For case, when this protocol is used, it is impossible to intercept the password hash then attempt to restore it, simply because no hash is communicated.
Apple uses SRP-6a, which is the most avant-garde version of this protocol. This version instructs to disconnect in case of failed authentication. In addition, Apple allows just ten authentication failures for this service and blocks all subsequent attempts.
A detailed description of SRP and its mathematical foundations is beyond the scope of this article. However, for completeness of presentation, hither is an case used past 'com.apple.Dataclass.KeychainSync' service.
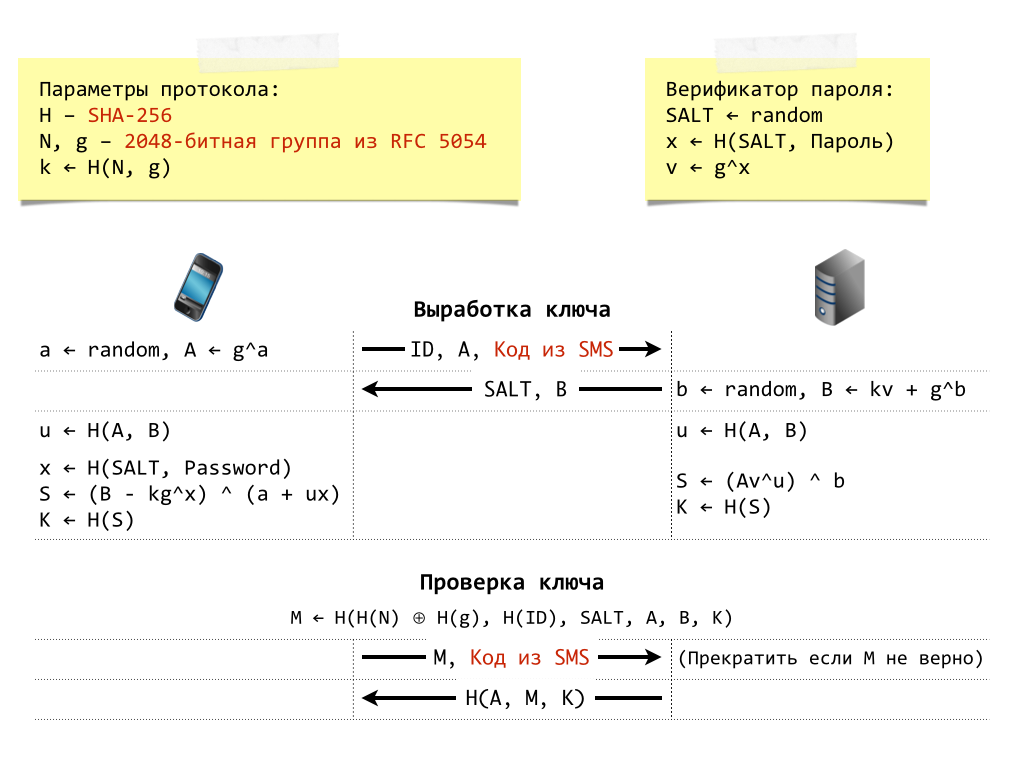
Example of SRP-6a used by 'com.apple.Dataclass.KeychainSync'
As the hash function 'H', information technology uses ' SHA-256' and, equally a group ('Due north', 'g'), it uses a 2048-bit group from 'RFC 5054' "Using the Secure Remote Password (SRP) Protocol for TLS Authentication". The protocol is run as follows:
- The device generates a random value 'a', calculates 'A=grand^a mod N', where 'Northward' and 'grand' are the parameters of 2048-bit group from 'RFC 5054', and sends to the server the message that contains the user 'ID', computed value 'A' and confirmation lawmaking from SMS. 'DsID' value, a unique numeric user ID, is used as the user identifier.
- Later receiving the message, the server generates a random 'b' value and computes 'B=k*v + g^b mod N', where 'k' is a multiplier specified in 'SRP-6a' as 'g=H(North, one thousand)', 'v=g^H(Common salt, iCSC) mod N' is the password verifier stored on a server (similar to the password hash), the 'Salt ' is a random table salt generated when creating the business relationship. The server sends a message to the client containing 'B' and 'Salt'.
- The customer and the server compute their shared session key 'G' through simple mathematical transformations. Afterward this, the first office of the protocolâ€"central generationâ€"is completed, and at present the client and the server must make sure that they have the same 'K' value.
- The client computes 'Thou=H(H(North) XOR H(g) | H(ID) | Common salt | A | B | Grand)' to prove that it knows 'K' and sends to the server the 'Thousand' value and verification lawmaking received from SMS. The server likewise computes 'M' and compares the value received from the customer with the computed value; if they do non friction match, the server terminates the protocol and disconnects.
- The server proves to the client that it knows 'Chiliad' by computing and sending 'H(A, M, M)'. Now, both participants in the protocol not only generated a shared key simply as well made certain that both of them accept the same key. In case of the escrow service, the server as well returns a random initialization vector ' IV ' and the escrowed record encrypted with the shared primal 'K' by using 'AES' algorithm in 'CBC' fashion.
In my opinion, the use of SRP for additional protection of user data substantially improves the organisation security confronting external attacks, if only considering information technology allows to effectively resist the attempted fauna force attacks against iCSC: during one connection to the service, y'all can try simply 1 countersign. Later on several failed attempts, the account (as part of working with the escrow service) is switched to soft lock state and temporarily blocked and, after ten failed attempts, the business relationship will be blocked permanently and any further piece of work with the escrow service tin can exist allowed only later resetting iCSC for the business relationship.
At the same time, the use of SRP does non, in any way, protect against internal threats. The escrowed countersign is stored on the Apple servers and, therefore, we can assume that Apple can gain access to it when needed. In this case, if the password has non been protected (for example, encrypted) before escrow, this may pb to completely compromising Keychain records stored in iCloud, since the escrowed password will let to decrypt the encryption keys and they, in turn, will allow to decrypt Keychain records (pay attention to 'com.apple.Dataclass.KeyValue').
However, in its "iOS Security" document, Apple claims that information technology uses specialized Hardware Security Modules (HSM) to store the escrowed records and that the access to escrowed data is impossible.
Escrow Security
iCloud provides a secure infrastructure for the escrow of Keychain which ensures the recovery of Keychain merely by authorized users and devices. HSM clusters protect the escrowed records. Each cluster has its ain encryption key that is used to protect the records.
To recover its Keychain, the user should pass the authentication by using his/her user proper noun and iCloud password, and reply to received SMS. When this is done, the user must enter his/her iCloud Security Code (iCSC). HSM cluster checks whether the iCSC is correct by using SRP protocol; and, in this case, iCSC is not communicated to Apple tree servers. Each cluster node, regardless of the others, checks whether the user exceeded the maximum number of attempts to recollect data. If in most of the nodes the verification is completed successfully, the cluster will decrypt the escrowed record and return it to the user.
Side by side, the device uses iCSC to decrypt the escrowed record and get the password used to encrypt Keychain records. With this countersign, the Keychain retrieved from Key/Value store is decrypted and recovered to the device. The organisation allows but 10 attempts to pass the authentication and think the escrowed information. Subsequently several failed attempts, the tape is locked and the user must contact the customer support to unlock it. After the 10th failed attempt, HSM cluster will destroy the escrowed record. This provides protection against animate being force attacks aimed at retrieving the record.
Unfortunately, we couldn't check whether HSM is really used. If it is actually so and HSM does not let to read their stored information, one can argue that the iCloud Keychain information is too protected from internal threats. Merely permit me repeat that, unfortunately, we cannot prove or refute the use of HSM and the impossibility to read their stored data.
Still, there is ane more way to protect your data from internal threats â€" by protecting the escrowed data on your device before sending it to Apple servers. Every bit it follows from the clarification provided by Apple (and the reverse technology confirms that), such protection is really used and the escrowed countersign is encrypted by using the iCSC before sending it to Apple servers. Obviously, in this case, the level of security (against internal threats) directly depends on the complexity of iCSC and a iv-character iCSC used past default does not provide sufficient protection.
Now that we found out how individual elements of the system operate, it is time to look at the system as a whole.
Putting it all Together
The diagram shows the escrow process and recovery of Keychain records in iCloud Keychain. The system works as follows:
- The device generates a set of random keys ('keybag' in Apple terminology) to encrypt the Keychain records.
- The device encrypts the Keychain records (which accept the enabled aspect 'kSecAttrSynchronizable') with a set of keys generated in the previous step and stores the encrypted records in Fundamental/Value store 'com. apple. sbd3' (cardinal 'com. apple. securebackup. record').
- The device generates a random password, which consists of six groups of 4 characters (the entropy of such a password is virtually 124 bit), encrypts the gear up of keys generated in footstep 1 by using this password and saves the encrypted set up of keys in Primal/Value store 'com. apple.sbd3' (key 'BackupKeybag').
- The device encrypts a random countersign generated in the previous step past using the key obtained from the iCloud security lawmaking of the user and escrows the encrypted countersign to the service 'com.apple.Dataclass.KeychainSync'.
When configuring his/her iCloud Keychain, the user tin utilize a circuitous or random iCSC instead of a iv-digit code prompted by default. When you apply a complex code, the mechanism of escrow arrangement does non modify; the just difference is that the primal for encrypting a random password will be computed not from the four-digit iCSC simply from a more complex lawmaking entered by the user.
In case of a random code, the password escrow engine is not used at all. Moreover, the random password generated past the arrangement is iCSC, which the user must remember and store safely. The Keychain records are encrypted and stored in Primal/Value store 'com.apple.sbd3' in the same way, but the service 'com.apple tree.Dataclass.KeychainSync' is not used.

Diagram of Keychain escrow and recovery engine
Conclusions
We can safely say that, from a technical point of view (i.e. without considering the possibility of social engineering science) and against the external threats (i.e. not Apple tree), the security of iCloud Keychain escrow service is at a sufficient level. The use of SRP protocol prevents the attacker from gaining access to Keychain records, even when the iCloud password is compromised, because such access additionally requires iCloud Security Code, and whatsoever brute force assault against this code is made significantly more difficult.
At the same time, by using some other iCloud Keychain mechanism, such as the countersign syncing, an attacker that compromised the iCloud password and has a brief concrete admission to one of user'south devices can also fully compromise the iCloud Keychain â€" all he/she has to practise is to add the assailant'due south device to the circle of trust of user'south devices and this can be washed only by knowing the iCloud password and having a brief admission to the user'south device in order to ostend the request to add a new device to the circle.
Every bit for protection against the internal threats (i.east., Apple or anyone else with admission to Apple servers), the security of escrow service does not appear so rosy. Apple tree's claims, that it is using HSM and the data stored on them cannot be read, are non supported by irrefutable testify, and the cryptographic protection of escrowed data is tied to iCloud Security Lawmaking, which is extremely weak in case of default settings and allows anyone who is able to think the escrowed records from Apple tree servers (or HSM) to virtually instantly recover the four-digit iCloud Security Code.
In case of a complex alphanumeric lawmaking, such attack becomes more difficult equally the number of possible passwords is greater. If iCloud Keychain is configured for using a random code, the escrow service is not used at all, which indeed makes this assail vector impossible.
The maximum security (excluding, of course, the selection of completely disabling iCloud Keychain) is ensured by using a random lawmaking â€" this is not because such code is harder to intermission with a brute force attack, simply because the password escrow engine is not used at all and, hence, the attack surface becomes smaller. Withal, the user-friendliness of this choice leaves much to be desired.
thomasforeadfat67.blogspot.com
Source: https://hackmag.com/uncategorized/in-the-depths-of-icloud-keychain/
Belum ada Komentar untuk "Icloud Couldnã¢â‚¬â„¢t Save Reply Try Again"
Posting Komentar